Windows Users Face Widespread Outages Due to Bug in Latest Crowdstrike Update
VTA-004490 – Windows Users Face Widespread Outages Due to Bug in Latest Crowdstrike Update
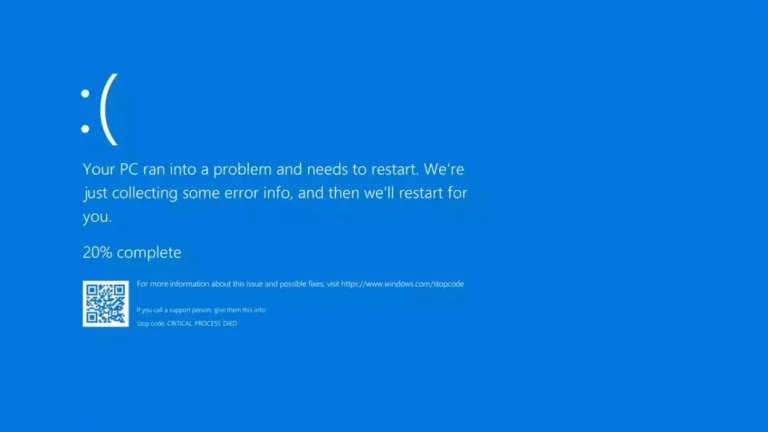
Windows users worldwide are experiencing significant disruptions due to a recent update from CrowdStrike, a cybersecurity firm. This update has led to systems crashing with blue screen errors and other performance issues, particularly in environments where Windows systems are critical for operations, such as airports and hospitals.
The issue originates from a bug in CrowdStrike’s Falcon sensor, related to its memory scanning prevention policy. This bug has caused the sensor to consume 100% of a single CPU core, leading to system slowdowns and crashes. CrowdStrike has acknowledged the problem and recommended rebooting affected systems to mitigate the issue
CrowdStrike has rolled back the problematic update and is working on a fix. In the meantime, they have advised users not to attempt sensor upgrades or downgrades without first rebooting their systems, as these actions will not resolve the issue and may lead to further complications
Severity:
High
Attack Surface:
N/A
Tactics:
Techniques:
T1068 – Exploitation for Privilege Escalation
T1140 – Deobfuscate/Decode Files or Information
T1562 – Impair Defenses
T1489 – Service Stop
T1485 – Data Destruction
T1203 – Exploitation for Client Execution
Indicator of Compromise:
N/A
References:
1. https://www.ndtv.com/world-news/windows-systems-restarting-throwing-blue-screen-of-death-due-to-crowdstrike-error-6138820
SuperPRO’s Threat Countermeasures Procedures:
1. Reboot Affected System as this is the primary step recommended by CrowdStrike to alleviate the high CPU usage issue.
2. Avoid Unnecessary Changes as users are advised against attempting to upgrade, downgrade, or uninstall the sensor before a reboot.
3. If the issue persists after rebooting, boot Windows into Safe Mode or the Windows Recovery Environment, navigate to the C:\Windows\System32\drivers\CrowdStrike directory, locate and delete the file matching “C-00000291*.sys,” and then boot the host normally.
4. Monitor CrowdStrike communications for further updates and patches to address this issue completely
Contributed by: Keevan