Home – PROVINTELL
NEXT-GEN CYBER DEFENSE
Threat Intelligence As First Line Of Defense
Copyright © PROVINTELL 2025

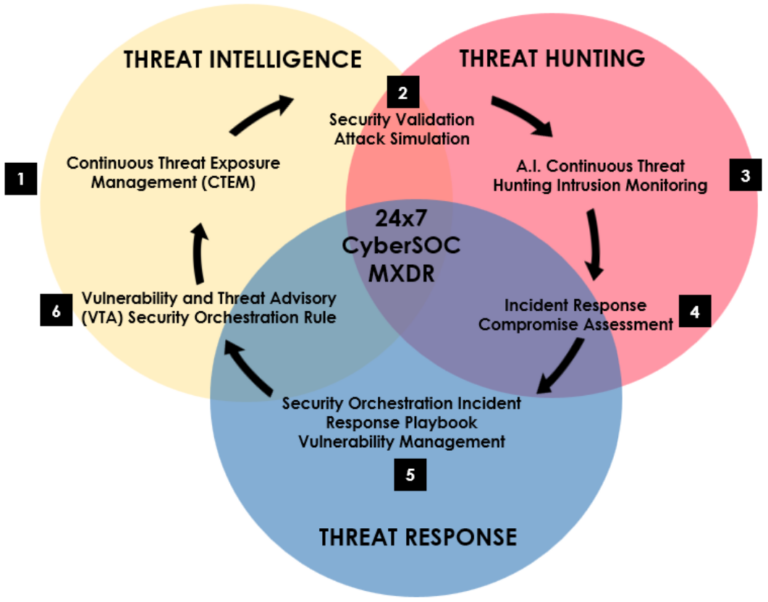
Continuous Threat Exposure Management (CTEM)
IDENTIFY
1. Identify your attack surface, data breach and exposure risk
External attack surface management of any organization which involves data collection processes and continuous monitoring of external threats, vulnerabilities anomalies of the publicly accessible application infrastructure and services, cloud storage and third-party services, public records and data breaches that would highly increase the exposure risk of any organization being the primary target of the cyber criminals.
Supporting organization in exposure risk management and attack surface reduction to protect business reputation and operations with good cyber hygiene practices

Vulnerability Management and
Security Validation
DETECT
2. Assess and reduce your exposure risk with vulnerability management and security validation
It is a fact that a threat only materializes when there is a vulnerability. Therefore, vulnerability management is essential to help organizations in continuously assessing and managing the security vulnerabilities in the clouds, networks and systems to reduce the exposure risk to cyber threats.
The security validation systems and techniques employed with operational threat intelligence of CODERED ASM would help organization in managing their cyber security risks more efficiently.
24×7 CyberSOC
Managed Extended Detection and Response
DETECT
3. Continuous threat hunting and intrusion monitoring with XDR Kill Chain and machine learning
How does an organization efficiently respond to cyber threats without breaking the bank? Open XDR is the key in collecting, processing and responding to the cyber threat data in the most complex environment that requires the Extended Detection and Response (XDR) components such as EDR, NDR, UEBA, SOAR and NG-SIEM, to name a few.
The XDR Kill Chain and Machine Learning technologies are the vital tools for our 24×7 CyberSOC teams in responding to threats more efficiently by reducing MTTR (Mean Time To Respond) and minimizing human error that is highly due to data and alerts fatigue. Machine learning helps to reduce the effort and time required for incident triage and fidelity analysis.


Compromise Assessment and
Incident Response
RESPOND
4. Compromise assessment and incident response with external and internal threat intelligence
With proper utilzation of the strategic, operational and tactical threat data attributes from the external and internal threat intelligence platforms, our CyberSOC is equipped with most of the essential data sources in assessing and responding to cyber threats for our customers, holistically from endpoints to clouds, and dark web.
24×7 CyberSOC
Managed Extended Detection and Response
RESPOND
5. Security orchestration and incident response playbook
Our CyberSOC teams operate based on 80:20 rule. 80% is in security orchestration and playbooks with the utilization of SOAR (Security Orchestration, Automation and Response) technology in responding to threats more efficiently with the minimum involvement of our customers, and the 20% is for the investigation and engagement with our customers for threat mitigation.


Vulnerability and Threat Advisories
RESPOND
6. Vulnerability and Threat Advisories (VTA)
CODERED VTA is Vulnerability and Threat Advisories to help you stay ahead of the dynamic cyber threats, empowering you with the latest threat detection and prevention techniques.