Newly Discovered OpenSSH Vulnerability Known As ‘regreSSHion’ Allows Remote Code Execution with Root Privileges Image Credit by Pixabay VTA-004491 – Newly Discovered OpenSSH Vulnerability Known As ‘regreSSHion’ Allows Remote Code Execution with Root Privileges CVE-2024–6387, dubbed “regreSSHion,” has been discovered …
CODEREDVTA

Vulnerability and Threat Advisories
“Security rules and techniques that helping you stay ahead of cyber threats”
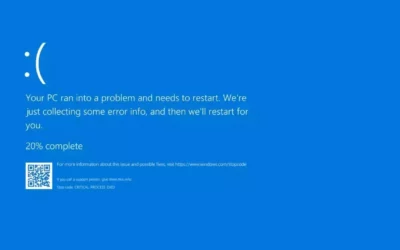
Windows Users Face Widespread Outages Due to Bug in Latest CrowdStrike Update
Windows Users Face Widespread Outages Due to Bug in Latest Crowdstrike Update Image Credit by Freepik VTA-004490 – Windows Users Face Widespread Outages Due to Bug in Latest Crowdstrike Update Windows users worldwide are experiencing significant disruptions due to a …
HardBit Ransomware 4.0 with Passphrase Protection and Advanced Evasion Techniques
HardBit Ransomware 4.0 with Passphrase Protection and Advanced Evasion Techniques Image Credit by Freepik VTA-004489 – HardBit Ransomware 4.0 with Passphrase Protection and Advanced Evasion Techniques In 2022, HardBit Ransomware released version 4.0, focusing on data theft, encryption, and ransom …
Emerging Malware Campaign named Poco RAT Targeting Users
Emerging Malware Campaign named Poco RAT Targeting Users Image Credit by Freepik VTA-004488 – Emerging Malware Campaign named Poco RAT Targeting Users A new malware campaign targeting Spanish-speaking users, named Poco RAT. This Remote Access Trojan (RAT) primarily attacks the …
China-Linked Group Exploits Cisco Switch Flaw for Malware Delivery
China-Linked Group Exploits Cisco Switch Flaw for Malware Delivery Image Credit by Pixabay VTA-004487 – China-Linked Group Exploits Cisco Switch Flaw for Malware Delivery A cyberespionage group possibly linked to China has leveraged a zero-day exploit in Cisco’s NX-OS software …